The US NSA’s PRISM program appears to be a set of specialized deep-packet inspection filters combined with pre-existing wiretapping points at high-level Internet carriers in the United States. Since the program’s revelation the day before yesterday, speculations have ranged far and wide about who does what to make this surveillance state nightmare possible. Adding it all together, it would appear that the social tech companies did not, repeat not, supply bulk data about their users at the US Government’s will – but that the situation for you as an end user remains just as if they had.
The day before yesterday, news broke – no, detonated – that the NSA named nine social communications companies as “providers” for spy data. Among them were Microsoft, Hotmail, Skype, Apple, and Facebook – no surprises there, activists in repressive countries say “Use once, die once” about Skype – but also companies like Google and Gmail. This raised a lot of eyebrows, not to say fury.
The idea that the companies you trust with your most private data were handing that data wholesale to today’s Stasi equivalents was mind-bogglingly evil and cynical. As the news of this broke, the companies would have been a lot better off if they had just been found out doing something like eating live children.
The impression that companies were playing an active part in providing private data to the NSA was strengthened by the precision of the presentation – that there were dates when each company had, as it seemed, voluntarily joined the surveillance program.
Seeing the companies in question scramble to deny the allegations of the NSA deck – first from on-duty spokespeople with their polished façade, then from CEOs – was the inevitable next step. But this is where things became interesting. While the initial polished façade was barely credible, the response from the CEOs came across as surprised, open, and candid.
So far, there are three parties to this story: the NSA with its leaked slide deck naming the nine companies as data providers, the media who reported on it, and the companies denying any active part in NSA spy activities. The first reaction is that at least one of them must be lying. But I don’t think any of them are. I think the leaked deck from the NSA is genuine, I think the Washington Post and Guardian didn’t conspire to make shit like this up, and I have come to believe the response from the companies. How could this be possible?
At this point, there are three possibilities of what PRISM is:
1: Social communication service companies are handing the NSA private data automatically, wholesale and/or on request. This was the initial impression from the deck and the Guardian / Washington Post articles, combined with NSA’s use of “provider” when naming the nine companies.
However, one interesting initial reaction from the companies in question said something quite relevant: “if this is happening, it is without our knowledge or consent”. That leads us to option 2.
2: The NSA is wiretapping a number of key junction points on the Internet in real-time, and have specialized real-time filters to extract information when people use services from the named nine social services companies. We already know about the fiber split box at AT&T, we know about Echelon, we know about at least one court order to Verizon. The fact that the Internet is wiretapped in real time by spy agencies is well-known. How that data is used and analyzed, not so much.
There is also a third option, which is the normal court route of getting a court order to give out a user’s private data, which the New York Times speculated was the Prism program:
3: When presented with a judicial order, companies abide with the law and present as much information as they are legally required, but not more. This has been the case for quite some time, and far predates social communications – and digital communications, for that matter.
Out of these, it would appear that options 2 and 3 are true. Option 1 is not. Here’s why.
When the CEO of Google and their chief legal officer publish a joint blog post named “What the Fuck?”, there’s an element of very candid surprise there. When they word their rebuttal to the allegations in a way that leaves absolutely no loopholes whatsoever,
Press reports that suggest that Google is providing open-ended access to our users’ data are false, period.
…then that comes across as candid fact. So just to empty all possibilities, could they be unwittingly lying – would it be possible for a low-ranking network administrator to have received a secret letter and order to comply with wholesale wiretapping? Would it be possible for the CEO to not know about this? In a word, no. No. That would not be conceivably possible with the traffic volume and patterns required.
Second, this slide from the now-infamous 41-slide NSA deck demands some extra attention:
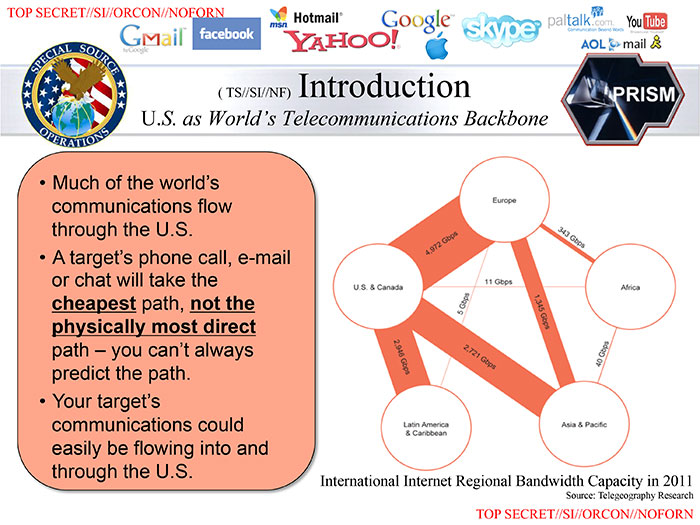
The 41-slide leaked presentation is allegedly used to introduce the PRISM program to people at the NSA. If companies were willfully handing over private data wholesale as per option 1 above, this slide – worldwide Internet routing paths and bandwidth – would be completely irrelevant noise to the presentation. However, if option 2 was true, this particular slide would be absolutely key to understanding how and why the program worked. You would not be able to make good use of the data analysis without understanding the limitations of how the data is being collected, and this slide answers that question perfectly, albeit at a high level.
This leads us to the following conclusions:
- The FISA court orders requiring disclosure of specific information for specific users are not PRISM. They exist, but are completely irrelevant to this discussion.
- The nine companies named as “providers” have not played the active part that the word implies, or any active part at all.
So in conclusion,
PRISM appears to be an analysis method of the catchall Internet wiretapping we already knew about, an analysis method that specifically targets traffic to and from nine social communications services.
This is obviously still just speculation from the currently available data, but it’s the way all the pieces of the puzzle so far appear to fit together.
The earlier conclusions that privacy is your own responsibility, and the dangers of using a centralized service, well, those conclusions completely remain. But the early notion that the centralized services were complicit in governmental spying appears to have fallen. Active part or not, though, the important part here is that you’re still being wiretapped. You’re still being wiretapped when using these services, regardless of who does the actual wiretapping and who assists and who doesn’t.
To some extent, encryption could probably mitigate the situation. Do you know how to encrypt all your traffic and data? Do you do it? If your answer is no, your social life is getting on file with today’s Stasi, which – by the way – was a German abbreviation for Ministerium für Staatssicherheit, translating literally to National Security Agency.



[…] The US NSA’s PRISM program appears to be a set of specialized deep-packet inspection filters combi… […]
[…] Rick Falkvinge beskriver lite närmare vad tekniken kan handla […]
Rick, as a response to your last questions in this article, could you point me to a place where I can learn about encrypting my traffic and data? Preferably understandable to someone who has experience with software and computers in general, but doesn’t know anything about cryptography and cybersecurity.
The NSA developed SHA (Secure Hash Algorithm), which is used in SSL, TLS and such secure protocols (which are in turn used by services such as Gmail, Google+ and others). Is it possible for the NSA to have a back door for reading data in plain text when such algorithms are used to encrypt data? If so, would it then be possible for the NSA to actually have full access to the data Google and others are accused of providing the NSA with, without the involvement of these companies?
J Persson, in short, no.
The algorithm for SHA is actually fairly simple to understand and has been vetted by thousands of security professionals. When someone publishes a new encryption algorithm it is usually quickly put to the test by cryptanalysts eager to break it and discover the information that is hidden behind it.
SHA is so widespread in use primarily because no one has figured out a good way to break it yet. Trust me people have tried. The NSA does not have a backdoor of any sort in the algorithm.
Something else to keep in mind as well. If they left some sort of backdoor, they would be exposing themselves to vulnerabilities too as they also make use of SHA. Those sorts of things don’t stay secret forever.
Is it your assumption that also default encryption levels are compromised here? Port 443 to gmail for example? Reply through mail highly appreciated. Hosted on gmail though 🙂
and on a further note, having access to trusted root certs in us would make is easier to read the datastreams. Google and so on were eager to deny .. has anyone asked the cert issuing authorities already their statements?
Having the root certs doesn’t give an adversary anything as far as decrypting data — certs are only for infusing a level of trust that somebody is who they say they are. You would need the server’s private key to decrypt the data.
However, with that said — it’s pretty easy for a site using TLS/SSL encryption to simply provide a copy of the private key to a third party.
Well, if option 2 is right, the NSA can act as a man-in-the-middle. If it also controls the root CA issuers, it can easily forge a response from Facebook, Google or whatever and thus make your pretty lock on the browser useless.
In such a scenario, the man-in-the-middle can access every data that your browser reads.
So that was a very interesting question: has anybody talked to the root CA issuers yet?
Not so fast…
I don’t think that the “Internet slide” necessarily has that meaning. It could be there as a description of the “old” methodology, perhaps pointing out its drawbacks and certainly describing its limitations. Also, if they “only” are spying on traffic in real time, the problems with encrypted communications would be huge.
1. The National Security Letters prohibit the reciever in any way disclosing the scurity letter or its contents. So lying is expected.
2. Westerners are so naive. Corporations lie. Blatantly. Or should (see naive). Don’t trust them.
3. Still I don’t believe the PRISM is what it is believed to be. It just doesn’t match what other leaks and rumours in the field say.
[…] So Just Exactly What Is NSA’s Prism, More Than Reprehensibly Evil … falkvinge.net/…/so-just-exactly-what-is-nsas-prism-more-than-reprehensi… 6 hours ago – The US NSA’s PRISM program appears to be a set of specialized deep-packet inspection filters combined with pre-existing wiretapping points … […]
Boundless Informant: the NSA’s secret tool to track global surveillance data
http://www.guardian.co.uk/world/2013/jun/08/nsa-boundless-informant-global-datamining#
NSA has repeatedly told Congress it can’t gather the very information Boundless Informant is designed to do. Lying to Congress ain’t good, especially when they supposedly carry out the oversight Obama says keeps everything above board.
And, as an aside, another creepy name : Boundless Informant
http://www.guardian.co.uk/world/2013/jun/08/nsa-prism-server-collection-facebook-google
« Some articles have claimed that Prism is not a tool used for the collection of information from US companies, but is instead an internal tool used to analyse such information.
Others have speculated – in the light of denials from technology companies about granting “direct access” to servers – that Prism operates through interception of communication cables.
Both of these theories appear to be contradicted by internal NSA documents.
In the interests of aiding the debate over how Prism works, the Guardian is publishing an additional slide from the 41-slide presentation which details Prism and its operation. We have redacted some program names.
The slide details different methods of data collection under the FISA Amendment Act of 2008 (which was renewed in December 2012). It clearly distinguishes Prism, which involves data collection from servers, as distinct from four different programs involving data collection from “fiber cables and infrastructure as data flows past”.
Essentially, the slide suggests that the NSA also collects some information under FAA702 from cable intercepts, but that process is distinct from Prism.
Analysts are encouraged to use both techniques of data gathering.
The Guardian’s initial reporting of Prism made clear the technology companies denied all knowledge of the program, and did not speculate on whether it would need such co-operation in order to work.
A far fuller picture of the exact operation of Prism, and the other surveillance operations brought to light, is expected to emerge in the coming weeks and months, but this slide gives a clearer picture of what Prism is – and, crucially, isn’t. »
Rick, from the facts presented it seems difficult to reconcile the Post’s claim that the companies joined PRISM voluntarily with the claim that they were unaware of the spying. It seems more likely to me that the National Security Letters used simply prohibit the companies from revealing the existence of the program even if asked about it explicitly, hence Google having to claim in court recently that they had received between 0 and 999 such letters in the past few years. Your thoughts?
This article is agreat effort to dismiss the real importance of all of this that is the leak itself. veryone with a good brain cells know for ages that google, microsoft, apple, adobe were created by the US goverment since the begining just for that, spying electronic worldwide. Real criminals will never use any form of standard electronics to do wrong. The US goverment and partbers are in reality trying to do industrial espionage in planet scale. It is time for people to take a serious action and stop using internet for a week to make them come back to real democracy.
all the excuses that are coming out from the USA and the UK are bollocks! the security agencies may well keep using the phrase ‘targeted person(s)’ but that is just to try to throw people off the trail. if i was being targeted, the security agencies would also target everyone around me, from God to the Devil and everyone in between that has/might have in the past or the future as well as the present, an association of some sort or other with me, even if it’s passing me in the street, sitting next to me on the bus or standing next to me in a queue. basically, that means that everyone is a target! no amount of denials or assurances is gonna make me feel any better or any different to now. i cant trust my own government let alone other governments they associate with, especially the USA. since what happened during the horrific and deplorable events of 9/11, the USA has become obsessed with terrorism, to the point that it doesn’t trust anyone, including it’s own citizens, suspecting every single one of planning some despicable plot. what they have ignored is, to my mind, that all they are doing is making their own citizens not trust the government. that’s ridiculous because if any disaster happened, man made or natural, who else are they going to depend on?
Plausible deniability eh. Two companies, both allegedly Israeli-based, Verint and Narus. This from Washington’s Blog:
At least two foreign companies play key roles in processing the information.
Specifically, an Israeli company called Narus processes all of the information tapped by AT &T (AT & T taps, and gives to the NSA, copies of all phone calls it processes), and an Israeli company called Verint processes information tapped by Verizon (Verizon also taps, and gives to the NSA, all of its calls).
Thus, technically the NSA is not doing the tapping, it’s been ‘outsourced’. Hence all the corporations involved AND the NSA can deny grabbing billions of records.
B
[…] that the US government is planning to add Dropbox to its Prism providers. As I write this there is some question as to what this means: are the providers willingly giving the NSA access to their users data or is […]
And for how long will you continue to have scripts from google on your own site? You are knowignly helping them out yourself, don’t you understand that. You have to clean up your own doorstep.
While a user can encrypt email between traffic between himself and the server, there is no guarantee the same can be said between servers or between the recipient and his server. Yes you could encrypt the message however the address data would still be sent in the clear and be used to target mail of interest. Encrypting mail is also problematic as it relies on the ability of both parties ability to encrypt/decrypt and not quote your message back in an unencrypted reply. There is the other point that as encryption is not universally used, use of encryption could flag the message for brute force decryption.
[…] från 1200-talet med dagens fajt om internet att göra? en fajt där USA kommit att spela en alltmer uppenbar skurkroll. Ja, nu kommer vi till det och härmed är en liten kulturhistorisk lektion att […]
NSA Whistleblower Edward Snowden interviewed 2013-06-06
http://narus.com/solutions/narus-nsystem
[…] http://falkvinge.net/2013/06/08/so-just-exactly-what-is-nsas-prism-more-than-reprehensibly-evil/ […]
The NSA needed a loot of HDD’s to store all the Data.
Do you remember the supposed fold in Thailand after which the HDD prices sky rocketed for almost 1,5 years?
Is it likely that they really needed 1,5 years to get production back up to speed?
Or is it more likely that they produced over a year HDD’s in secret for the NSA?
Just some food for thoughts.
David X.
David,
While you are absolutely right to be extremely suspicious of the control freaks behind all this mass surveillance, I can assure you you the floods in autumn 2011 really did happen in Thailand. Not only was the HDD factory flooded, so were lots of others to the north of Bangkok, notably Toyota and Honda. How do I know? I experienced driving through the flood waters and having to guess where there might be deep water.
Not that I’d buy into that, but to play devil’s advocate:
He didn’t claim there was no flood. He claimed that cleaning up and ramping production back up couldn’t take *that* long as they claimed it did. Hence leaving a time gap between resuming production at full throttle and *publicly*admitting* to resume at full throttle. Which could be used to produce a helluva lot of HDDs off the record.
Wiretapping optical fibers perhaps?
Remembered that I had read something about a patent beeing approriated by government “Crater Coupler patent” before;
http://www.wired.com/science/discoveries/news/2005/09/68894?currentPage=all
//Lucke
Från kommentarsfältet på The Guardian:
Flash!!! The Air Force is Prohibiting Its Service Members from Reading About the NSA Scandals. By WND.
“President Obama has said the outrage over the federal government’s decision to monitor citizens’ phone activity is all “hype. He might want to share his opinion with the U.S. Air Force, which is ordering members of the service not to look at news stories about it.”
Read more at http://www.wnd.com/2013/06/military-told-not-to-read-obama-scandal-news/#JLM01qx2U0TYfr8T.99
But you havent pointed out how they can monitor these sites just be sucking up all their traffic. They use https encryption and its not trivial to break. Then again this is the NSA we’re talking about.
True, but as I said on a previous comment, if the NSA can act as a man in the middle and if it controls the root CA issuers, SSL is useless.
But won’t that be a harder blow to traditional banks than to cryptocurrencies? I mean you don’t need SSL to do BTC transactions but you need them to do credit card transactions online.
In theory, yes. In practice it won’t harm the banks as long as nobody knows or cares. It’s pretty much the same as fiat money: It’s basically a scam, but as long as everyone plays along, it won’t blow up in our face.
[…] So Just Exactly What Is NSA’s Prism, More Than Reprehensibly Evil? […]
Excellent article – makes good sense in the light of what little we know. Boo to the inattentive readers trying to accuse you of whitewashing Google. They seem to have missed your key point – that the threat exists REGARDLESS of whether the “providers” cooperate willingly, and must be dealt with accordingly. The big question in my mind is how much direct human intervention is needed in the PRISM analysis. Having a large quantity of tapped data in the hands of bureaucrats annoys me but fails to scare me – the result is a flood of Daisy Mae Schmedlap’s tweets about her latest cosmetic purchases (99.99999%) and possibly significant data (the rest – I’m having trouble keeping count). The ability to recognize those significant data is the crux of effective surveillance and repression, and the crux of defending against it is to learn how to spoof the method. When it was reported that surveillants were looking for key words and phrases in email, Internet activists flooded the network with emails with phrases like “k..l the p……t” and the like, hopefully generating mountains of false positives that long-suffering human analysts would have to go through to eliminate them. Something of the sort needs to be done with PRISM.
[…] So Just Exactly What Is NSA’s Prism, More Than Reprehensibly Evil? […]
Another question people need to be asking is this: have any SSL Certificate Authorities handed over private keys of entities like Google and Facebook to the USG?
CAs sign the *public* keys of their customers. They are not given the private keys (unless the customer is a complete idiot, which can happen.).
The CA-side risks are the possibility that a CA may have either given *its own* private key to an attacker (possibly unintentionally), thus enabling the attacker to generate their own fake certs, or that a CA may have signed a certificate request on behalf of an attacker (which has been known to happen, usually as a result of the attacker tricking the CA into signing it.)
I just could not leave your site prior to suggesting that I really loved the standard information a person supply in your visitors?
Is gonna be back ceaselessly in order to check up on new posts
Your long understand likewise discovered tumors may well from on
distinctive sites not ever as a rule suffering
from Warts, particularly liver organ, kidney, and moreover flesh.
Exceptional identified slots on non-Hodgkin and in addition
Hodgkin lymphoma while in the sample investigation.
Wide-spread parameters established certainly likely points why
back linking due to photos genital warts.
Hi, I think your website might be having browser compatibility issues.
When I look at your blog in Opera, it looks fine but when opening in Internet Explorer, it has some overlapping.
I just wanted to give you a quick heads up! Other then that, amazing blog!
What’s up to every body, it’s my first go to see of this blog; this web site includes remarkable and
genuinely fine stuff in support of visitors.
Good article. I’m dealing with some of these issues as well..